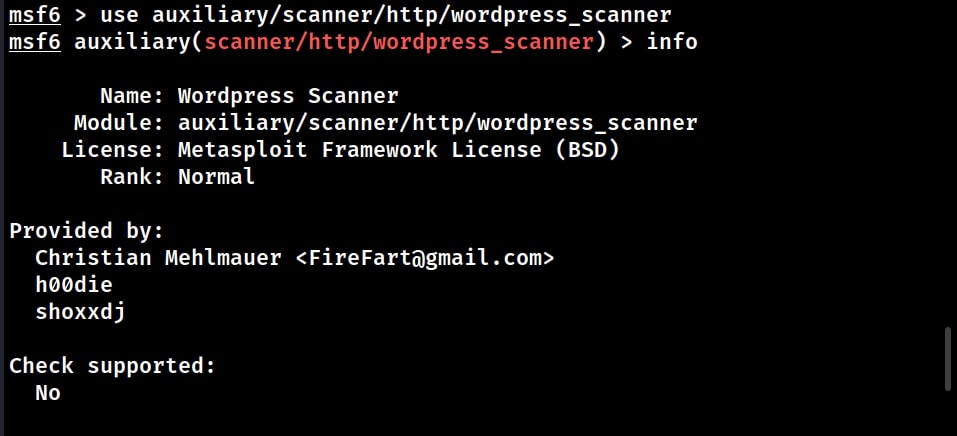
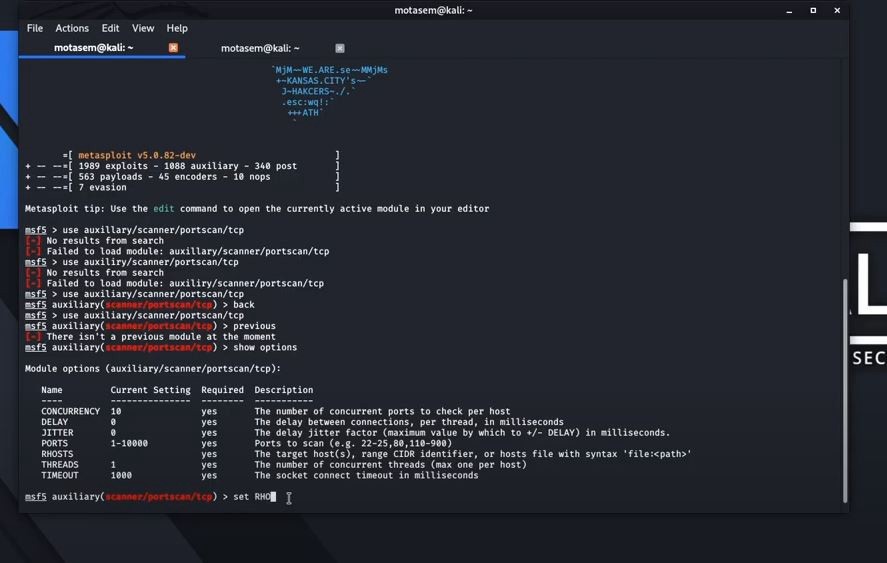
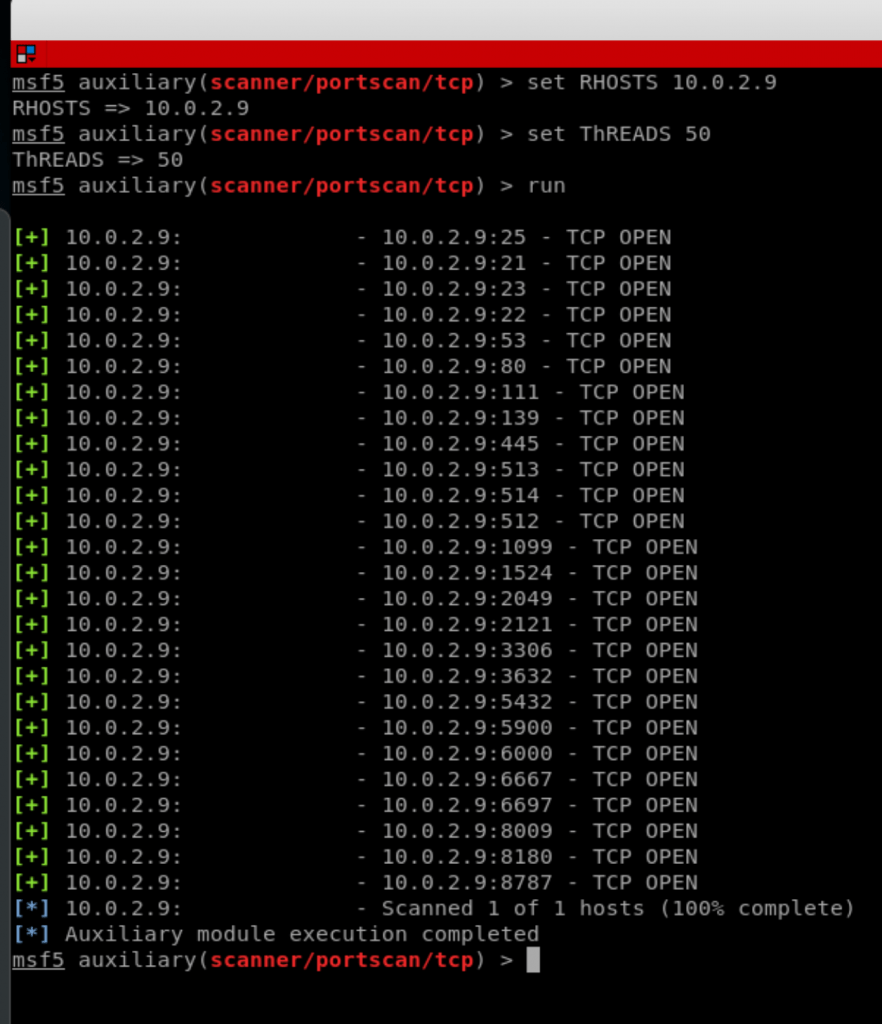
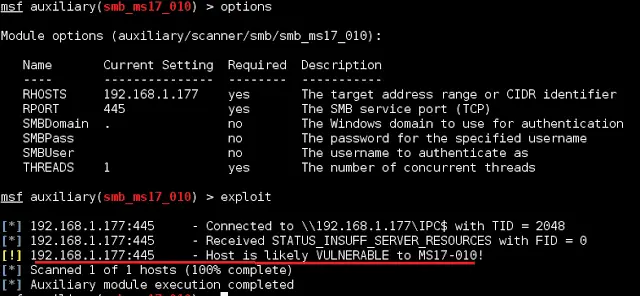
![Metasploit Auxiliaries for Web Application enumeration and scanning - Metasploit Revealed: Secrets of the Expert Pentester [Book] Metasploit Auxiliaries for Web Application enumeration and scanning - Metasploit Revealed: Secrets of the Expert Pentester [Book]](https://www.oreilly.com/api/v2/epubs/9781788624596/files/assets/15d23931-4396-4e2e-8b6e-6c4a90c7f021.jpg)
Metasploit Auxiliaries for Web Application enumeration and scanning - Metasploit Revealed: Secrets of the Expert Pentester [Book]

ScanAvenger - Scanner portatile wireless Bluetooth 3 in 1, senza fili, con pistola di scansione 1D per la gestione dell'inventario, senza fili, portatile, lettore di codici a barre : Amazon.it: Cancelleria e

High Precision "cat's Eye" Auxiliary Scanning Light 2d Barcode Scanner Support Hands-free Mode And Handheld Mode - Tool Parts - AliExpress
Total.js Directory Traversal. Metasploit framework is the most… | by Ashish Bhangale | Pentester Academy Blog




![MODE-01 Result [MODE-01:auxiliary/scanner/mongodb/mongodb_login] | Download Scientific Diagram MODE-01 Result [MODE-01:auxiliary/scanner/mongodb/mongodb_login] | Download Scientific Diagram](https://www.researchgate.net/publication/343215657/figure/fig8/AS:917412916514836@1595739692391/MODE-01-Result-MODE-01auxiliary-scanner-mongodb-mongodb-login.png)