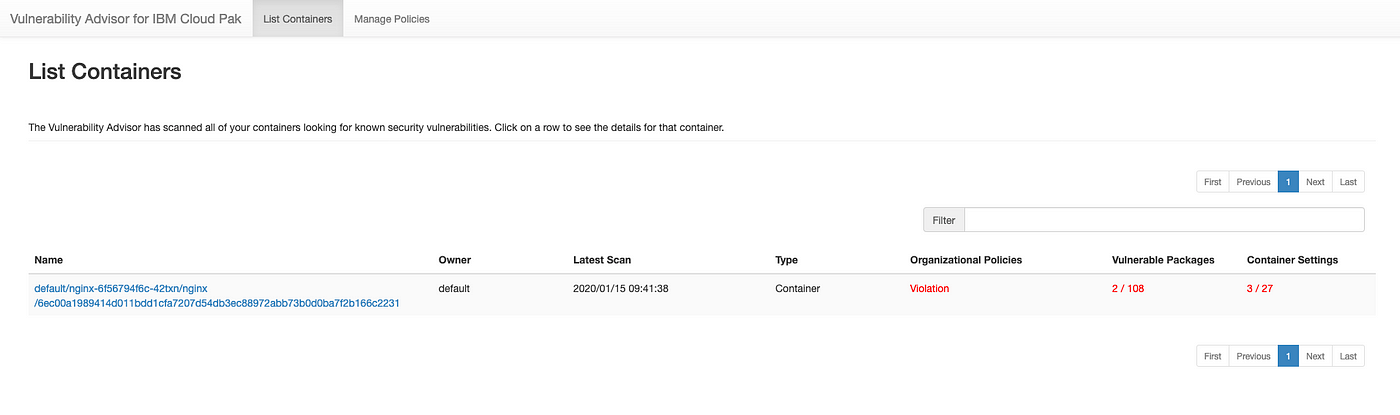
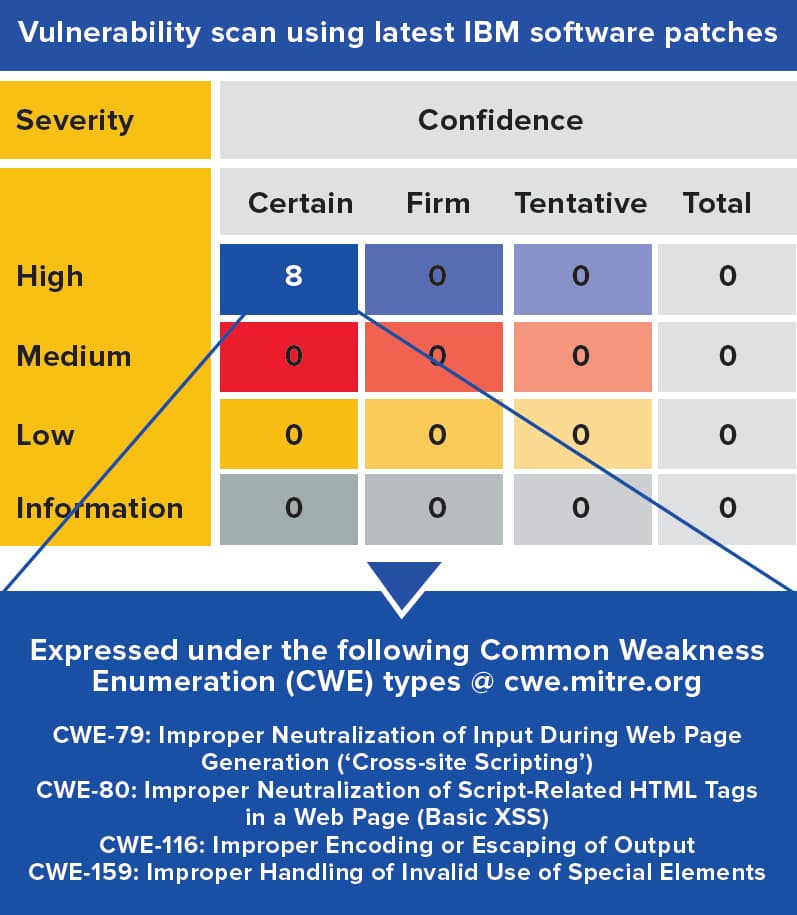
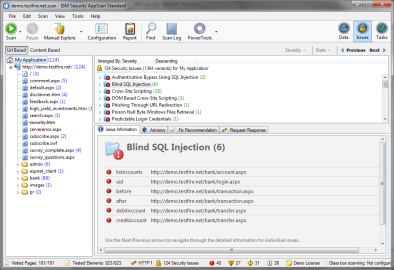
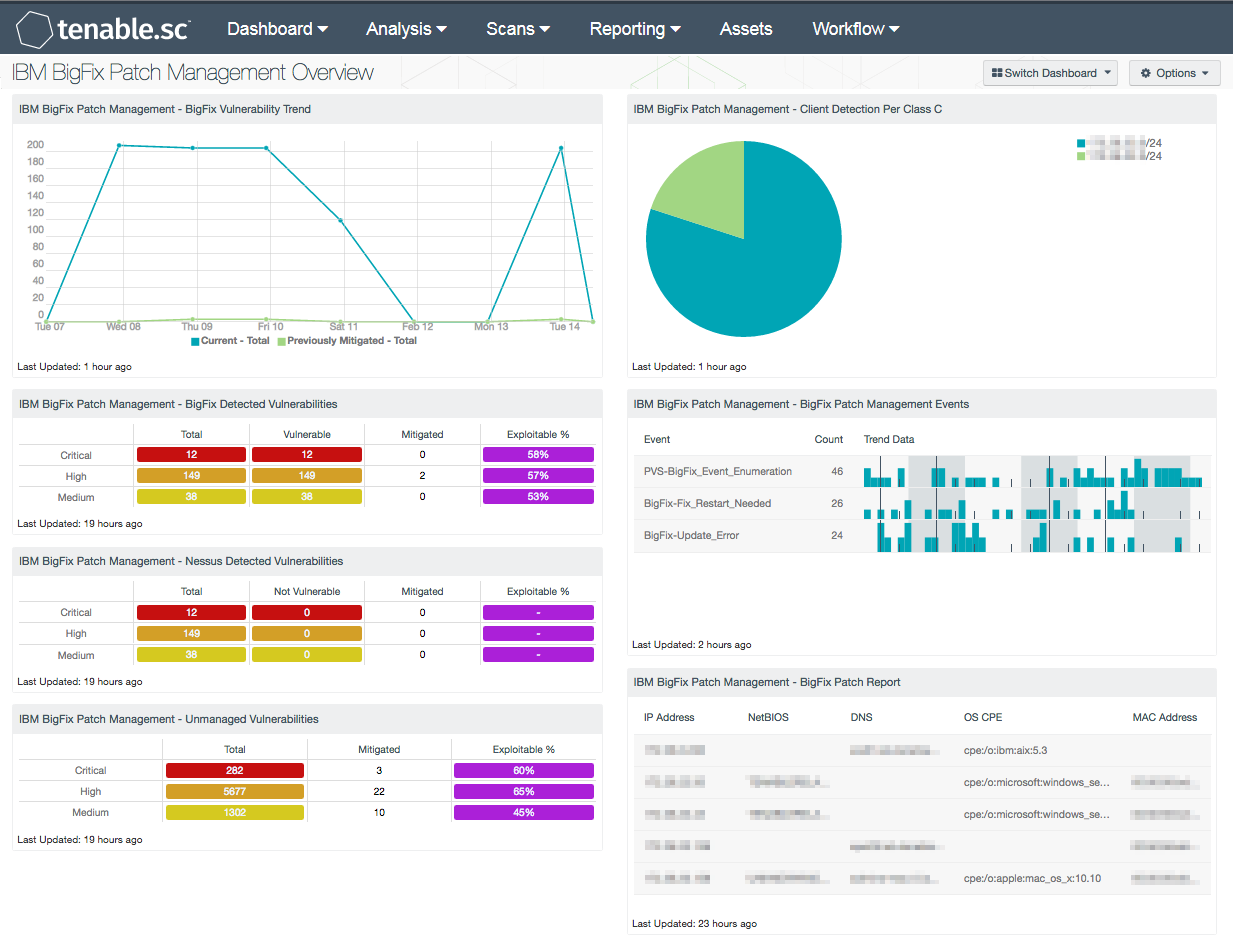
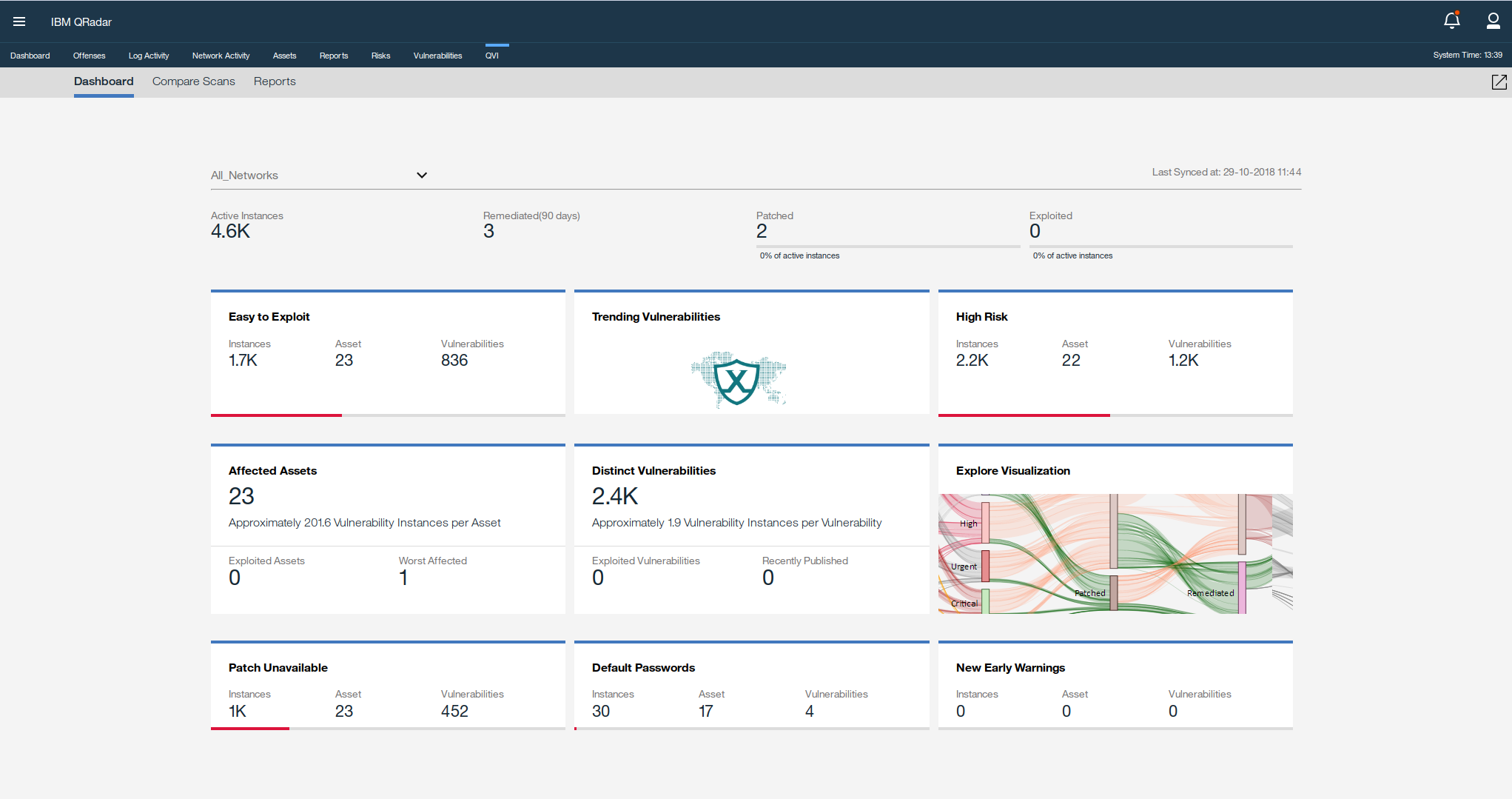
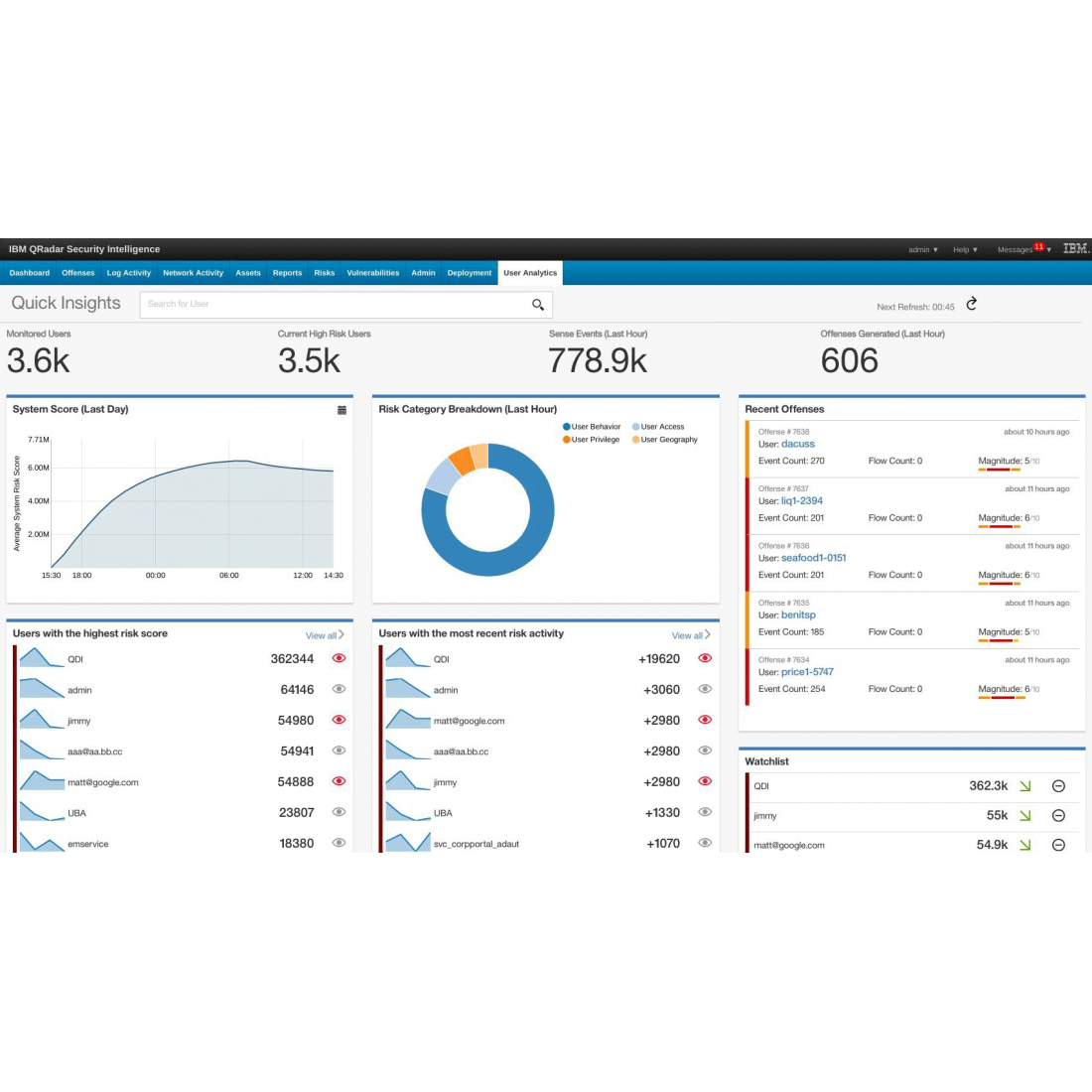
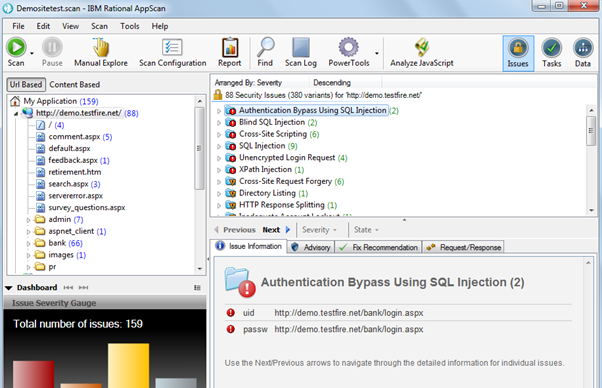
Vulnerability Scanning for Images and Running Containers on Red Hat OpenShift with Vulnerability Advisor | by Chen Nan Li | IBM Cloud | Medium

Vulnerability Scanning for Images and Running Containers on Red Hat OpenShift with Vulnerability Advisor | by Chen Nan Li | IBM Cloud | Medium

Intranet Security Vulnerability Scanning Tools Market Size, Booming Worldwide By KeyPlayers-Symantec, Intel Security, IBM
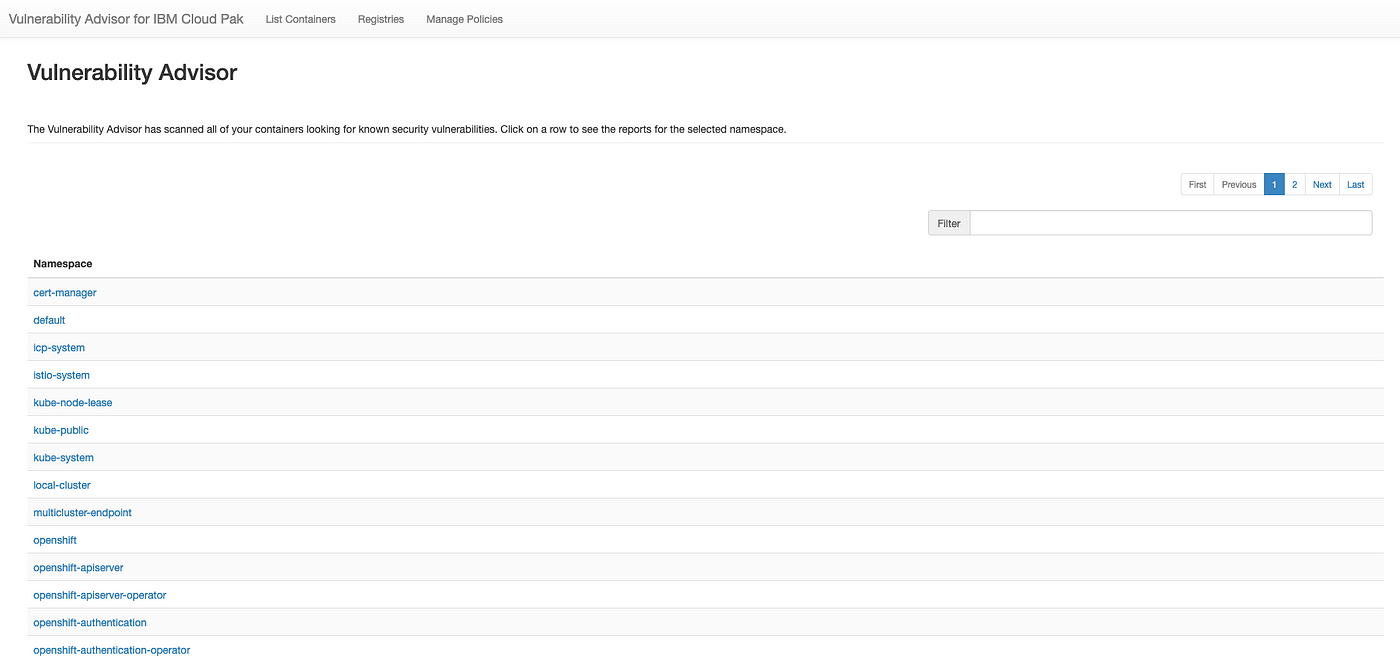
Vulnerability Scanning for Images and Running Containers on Red Hat OpenShift with Vulnerability Advisor | by Chen Nan Li | IBM Cloud | Medium